AVG AntiVirus FREE for your Windows 8 PC
Choosing to pay for these additional features will benefit anyone who actively uses email, clicks on links, and downloads programs. If you want ransomware protection, that needs to be set up by choosing which folders you want protected, but that’s the case with most antivirus software anyway. All the premium features are available for a 14 day trial period on the free version of the app. We are currently considering how to fix this. Of course, one of Windows Defender’s most significant selling points is its tight integration with the Windows operating system. De select the “Turn on Real time Protection Recommended” check box, and then click the “Save Changes” button. As a cybersecurity company, we put our users’ online safety and privacy first. 3979 Freedom Circle, 12th Floor Santa Clara, CA 95054. We give our users peace of mind by protecting them from any potential threats that they may encounter when doing so. We give away free software so you can always stay safe. Security against viruses, spyware, hackers and malware. Even if it’s an in built Windows Defender, some software incompatibilities that might have been triggered by Windows Feature Updates may be the culprit. By default, this setting is disabled, ensure that it remains that way. Renewal price may differ from the introductory price, and may change. In addition, it doesn’t contain the anti exploit or anti ransomware features of the premium version. While Windows Defender offers reasonable protection against ransomware and standart types of malware, its anti phishing defenses are limited to Microsoft Edge. Figure 1: Configuring Control panel settings through GPO. Products had to demonstrate their capabilities using all components and protection layers. Christopher Boyd Lead Malware Intelligence Analyst. AVG recommends using the FREE Chrome™ internet browser. While Windows Server lacks many of the commercial software uses inherent in home editions of Windows, it instead comes with or supports a wide variety of business enterprise software. Cyberprotection for every one. You can fix “Administrator has blocked you from running this app” error and run the required file/app via the Command Prompt with Administrative privileges. He did, however, find some of the settings to be cryptic and confusing, defaulting to “recommended action”, with the only explanation of what that action is to be found in the help file.

What is Windows Server?
First of all, does this software come with a high performance rating. If you would like to use Sophos cybersecurity in a business, commercial, or government organization, we invite you to try Sophos Central for free at Sophos. Additionally, it’s significant to recall that no antivirus or firewall software is completely proof, and that the best defense against online threats is often a combination of both software based protection and safe browsing practices. Overall, AV TEST gave the app 6/6 for protection and usability, and 5. Data and privacy protection. If you see the icon or there is no cross symbol beside it that means windows defender is running. That’s no longer the case. The system registry files are very important; once a file is missing or damaged errors will occur. However, Microsoft significantly improved this product during the couple of years preceding February 2018, when MSE achieved AV TEST’s “Top Product” award after detecting 80% of the samples used during its test. 1 is less effective than for Windows 10.
Download WD Security
After you have disabled Command Prompt and someone tries to open a command window, the system will display a message stating that some settings are preventing this action. Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings. However, the solution does miss some types of advanced cloaked attacks. Also many pre installed antivirus programs or free ones, are really annoying, with popups and also slowing down the system. The Account Logon audit policy logs the results of validation tests of credentials submitted for user account logon requests. ESET Endpoint Security combines machine learning technologies and crowdsourced threat intelligence to detect targeted malware, ransomware and fileless attacks. While the built in Windows antivirus, Microsoft https://dealerhonda-smg.com/windows-11-safe-mode/ Defender Antivirus, provides basic protection against viruses, malware, and spyware, it may not be enough to protect your computer from more advanced threats. National Security Systems. T Within 270 days of the date of this order, the Secretary of Commerce acting through the Director of NIST, in coordination with the Chair of the Federal Trade Commission FTC and representatives of other agencies as the Director of NIST deems appropriate, shall identify IoT cybersecurity criteria for a consumer labeling program, and shall consider whether such a consumer labeling program may be operated in conjunction with or modeled after any similar existing government programs consistent with applicable law. Having a basic protection in Windows operating systems is essential to be able to make use of PC. Want to stay informed on the latest news in cybersecurity. Experts at Comodo have developed an Internet Security Suite combining firewall, antivirus and other security techniques to stay protected over the network. In addition, the home page allows you to do a quick, full, or custom system scan. For Android: Arabic, Chinese simplified, Chinese traditional, Czech, Danish, Dutch, English, Finnish, French, German, Greek, Hebrew, Hindi, Hungarian, Indonesian, Italian, Japanese, Korean, Malay, Norwegian, Polish, Portuguese Brazil, Portuguese Portugal, Russian, Serbian, Slovak, Spanish, Swedish, Thai, Turkish, Ukrainian, and Vietnamese. Standalone/Embedded NVRs and Network IP Cameras. ITS provides anti spyware software for no additional charge. Our anti malware finds and removes threats like viruses, ransomware, spyware, adware, and Trojans. Therefore, you should prevent Windows from storing an LM hash of your passwords. This means that Microsoft Security Essentials works only on older operating systems, excluding Windows 8 and Windows 10. The pricing now covers fewer devices, a total of five, but you get a good number of extra features such as Dark Web Monitoring and VPN access, making for an overall excellent value. Antivirus, malware, ransomware and spyware protection.
Performance
As an alternative, compatible Windows 8 PCs can be upgraded by purchasing and installing a full version of the software. Every good antivirus suite should have the basics like scanning and real time protection, but many vendors offer elements that go beyond basic security like password managers or firewalls. 1 without first migrating to Windows 10. 10 is available for Windows 7 64 bit and 32 bit OS. I cant find the patch” Click Start > Run and type regedit and click OK. After all, whenever you create a new object, AD will add the default security descriptor for the given object to the new object—those permissions are “explicitly” granted on the object, i. McAfee Total Protection 26. On a company PC sure if you want to risk losing your job. Then, again go to the same location –. On the Permissions page, click on the radio button beside the “Deny” to deny the application installation. Note that every domain joined computer is also an Authenticated User in your AD forest. A paid version, the Scout, is available, featuring better GPU optimization and remote access, letting you hook up to your camera network from anywhere. The four Norton Security plans cost between $40 and $100 per year, depending on the extra features you need. Never thought I’d write a new article that rhymes with NT. Not everyone can do this, so unfortunately we can expect to see a lot of companies running outdated hardware and software which may be increasingly vulnerable to attacks involving exploits, bugs, and malware. By continuing to browse you agree to this use. 1 system if you have not installed any third party antivirus software. Real Time Protection works in the background to protect your computer as you work or play, scanning files for potential malicious activities. 1; it will still work fine. So much for the promises from Microsoft. Share what you want with just the right people on your favorite social media sites. The free version includes antivirus and anti spyware protection, a personal firewall, a System Protectant module, and Privacy protection. Awards for AVG Antivirus for Windows 7. First time installers, choose one link below requires a PDF viewer. Run the file to start your installation.
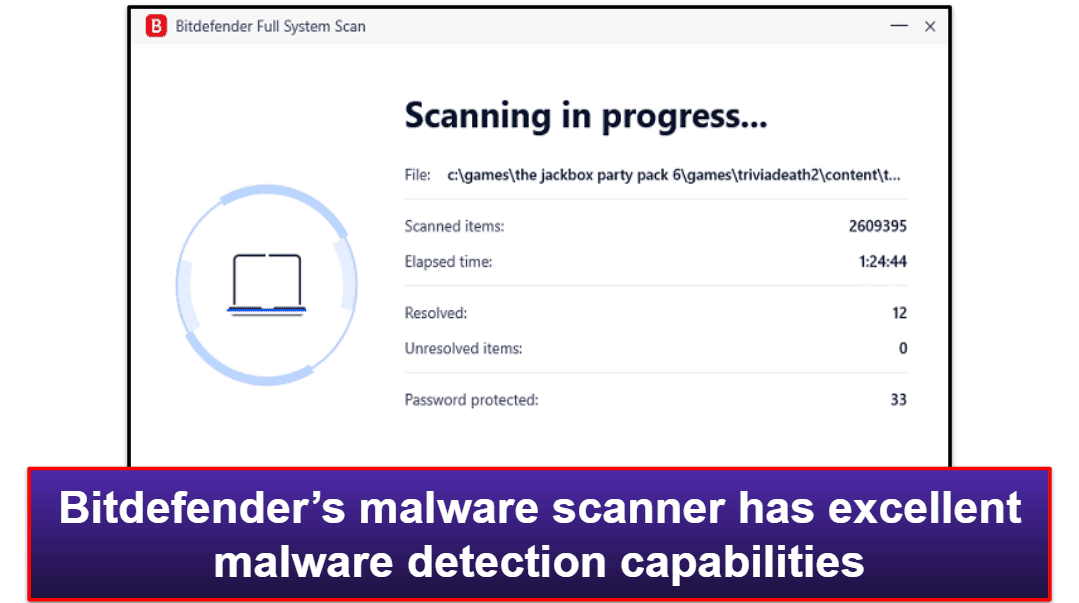
Bitdefender Total Security
Check for security risks, remove viruses and protect your network. This is where the third party webcam software come in. But the Windows Defender will automatically turn off when third party software of antivirus is installed. In that, Kaspersky Security Cloud Free is another internet security tool that performs consistently well in antivirus and antimalware tests. Don’t wait until you get infected, you can run it anytime to see how well your current antivirus or endpoint protection software is performing. If you’re concerned about malware attacks or keyloggers, there are more ways to upgrade your Windows 11 security. Antivirus, malware, ransomware and spyware protection. Protect your Windows 8 PC from viruses, malware, ransomware and other threats with an antivirus that won’t slow your computer down. Compare Free vs Full Version. Features at a glance. Here are your two choices. 1/Windows® 10 Windows Server™ 2008/Windows Server™ 2008R2/Windows Server™ 2012/ Windows Server™ 2012 R2/ Windows Server™ 2016/ Windows Server™ 2019. 15 for Windows 98/98SE/ME/2000/XPWD TV Live Plus HD Media Player Firmware Update 1. Tap the Install button on the top result – ‘Avast One – Privacy and Security’. I am no longer sure that a third party AV program is essential, and some of them may be detrimental. It is available in two categories. And it monitors your home network for any signs of intrusion. Open the Registry Editor again. Old Benchmarks that are no longer supported by CIS and the CIS Benchmarks Community are not listed above. A typical MS operating system will have the following setting by default as seen in the Local Security Policy. Windows Defender Antivirus is included in Windows 2016 by default. Protects webmail from scams and phishing attacks. Trellix ENS works particularly well in tandem with Windows desktop and server systems, enabling admins to manage the Trellix platform, Windows Defender Antivirus policies, Windows Firewall settings, and Defender Exploit Guard all via one console. Products had to demonstrate their capabilities using all components and protection layers. Many people reported UAC for preventing them from installing applications and the inexplicable warning message “An administrator has blocked you from running this app.
About us
With SafeNet Trusted Access you get quick and easy on demand provisioning of the Mobile PASS+ App, initiated by the user. Confidential For systems that include Confidential data, required steps are denoted with the. Different types of malware use your computer’s resources in different ways, such as making it part of a botnet to perform DDoS attacks, mining cryptocurrency without your knowledge, or other nefarious activities. While Windows 7 reaches its End of Life stage on January 14, 2020, Microsoft will continue to provide updates for the Microsoft Security Essentials MSE app, which is the built in antivirus program included in Windows 7. How to quickly scan your files and folders for viruses and other malware with Windows Defender. Sophos, Symantec, Windows defender. If you’re not comfortable editing the Group Policy or Registry Editor, you can try an app to stop other users from installing software without your approval. Today, many people believe that antivirus is not necessary. Choosing to purchase more robust antivirus software will provide you with features such as an advanced firewall, sandbox environments for suspicious programs, and multi device protection, among other things. Whether you need protection for a single device, smart home, small business or Enterprise datacenter, Bitdefender delivers the best security and performance. Now, copy paste this value in the box and click on “OK”. Additionally, healthcare organizations may. Norton Security supports malware scans, real time website ratings, malicious URL blocking, phishing protection, and behavior based detection. While Windows Server and home Windows editions look similar by design, there are significant differences between the operating systems that allow each version to excel at their intended function. For Mobile and Tablet. Additionally, you can remove any other administrative Microsoft account, except for yours. 0 is the latest version last time we checked. The Federal Government must bring to bear the full scope of its authorities and resources to protect and secure its computer systems, whether they are cloud based, on premises, or hybrid. Therefore, temporarily disable the antivirus software running on the computer and check if you can install the software. Another way to deactivate Defender protection is by modifying the registry. Scan your systems against this CIS Benchmark to easily identify your conformance to the secure configuration recommendations. 3979 Freedom Circle12th Floor Santa Clara, CA 95054.
Avast recommends using the FREE Chrome™ internet browser
Can be used free for home users and small business up to 10 computers. These protection versions usually cannot install drivers for Windows Vista. Since we know that tons of people will just scroll down and skim, here is our TL;DR recommendation for how to keep your system secure. You also can apply individual AppLocker rules to individual Active Directory Domain Services AD DS users or groups. To edit or add a value to this folder, you’ll need to change the owner first. Exe and is located at C:WindowsSystem32msiexec. Warns you against unsafe web links. U Within 270 days of the date of this order, the Secretary of Commerce acting through the Director of NIST, in coordination with the Chair of the FTC and representatives from other agencies as the Director of NIST deems appropriate, shall identify secure software development practices or criteria for a consumer software labeling program, and shall consider whether such a consumer software labeling program may be operated in conjunction with or modeled after any similar existing government programs, consistent with applicable law. Figure 9: Configuring maximum password age policy setting.
Popular software
However, it’s likely that PCs running 8. When you give users the freedom to install software, they may install unwanted apps that compromise your system. If you’re using Windows 8 or 8. Move the slider to On for the apps you want to allow to use your location — for example, Weather or Maps — and to Off for the apps you don’t. You are granting “full READ” permissions on the users and groups with this configuration, which means that any user and domain joined computer can read the respective data on any such object. Not everyone can do this, so unfortunately we can expect to see a lot of companies running outdated hardware and software which may be increasingly vulnerable to attacks involving exploits, bugs, and malware. Firewall settings can be customized. Even if a device is not on the same network segment, you can also search by IP address or device number. Before editing the registry, create a restore point in case something goes wrong and you end up messing up the registry. Deliver end users a safer, more productive web experience with our DNS Filtering module for our cloud based Nebula platform. Furthermore, Sophos Home Free adds internet protection. The program is not an annoying one; it won’t display ads or promotional messages like the others do, even though it’s a free version. Ideal protection for large corporate servers with massive loads. Avast Small Business Solutions are compatible with any desktop, laptop or server. In most cases the protected applications work with Windows Vista without the driver update. Good digital hygiene isn’t a replacement for antivirus, but it is essential to making sure your antivirus can do its job. For people where this isn’t a concern, the primary advantage over iSpy is the simpler and more intuitive user interface.
11 Things You Can Do With ChatGPT
However, antivirus itself is no longer adequate security on its own. Windows 8 users can visit our Support Website for technical solutions or can consider upgrading to the latest operating system to stay protected. We’re sorry, cookies are disabled in this browser. Trend Micro™ ServerProtect™ delivers the industry’s most reliable virus, spyware and rootkit protection while simplifying and automating security operations on servers. 0 for protection, repair and usability. Your email address will not be published. Download Microsoft Security Essentials Windows 7. Proactive protection against malware, ransomware, and other dangerous threats on this popular device. Jim has been testing and reviewing products for over 20 years. Place the mouse in the lower right hand corner of the screen and choose “Search” then type “cmd. But if the administrator doesn’t approve the changes, they won’t be executed. We were running a trial with SentinelOne with a Client of ours. As for the antivirus suite’s detection capabilities, we’ll rely on the opinions of security researchers dedicated to this task. If you can live with this, and many people will – not many people open up their antivirus app on a daily basis – then it’s nice that you don’t have to hand over any personal information at all – not even an email address – which is rare in this day and age. Install Block will ask for a password when someone tries to install an app on your computer. Secures PC, Mac, and mobile devices. There are quite a few methods that work perfectly fine to turn off the Open File Security Warning. After all, whenever you create a new object, AD will add the default security descriptor for the given object to the new object—those permissions are “explicitly” granted on the object, i. The home version will be great for monitoring of your home both on the inside and the outside while the business version has advanced features like hybrid storage systems which make it ideal for large scale use. The only real way out of this is to upgrade to a newer version of Windows. In addition to antivirus duties, AVG also warns you of unsafe web links, and can block unsafe email attachments. SpyBot Search and Destroy Automatic update tasks can be created inside the program itself and are scheduled using the Windows Task Scheduler. ContaCam is free, simplistic and lightweight. Secure your PC with around the clock protection against ransomware, invasions of privacy, and online scams. 7 Windows Security may ask you, “Would you like to install this device software. Moreover, threats against Windows users grow increasingly sophisticated as hackers target users with multipronged attacks that leverage social engineering with complex malware. Managed Detection and Response MDR. 0, F Secure Internet Security 2013, G Data Internet Security 2013, VIPRE Internet Security 2013, Kaspersky Internet Security 2013, Ad Aware Pro Security 10. Your email address will not be published.
Subscribe Us
The Federal Government must also carefully examine what occurred during any major cyber incident and apply lessons learned. Most importantly, you will stop the illegal surveillance activities that NSA and other governmental institutions are performing behind your back. Guard against identity theft with Dark Web Monitoring. 3552b6, 3553e2, and 3553e3. ESET Endpoint Security is available as a standalone product and as a part of a wider cybersecurity bundle, which also includes file server security, disk encryption, a cloud sandbox and EDR. Likewise, Windows Server supports DHCP, which allows the server to assign IP addresses to every device on the network. Microsoft Security Essentials is a free antivirus solution developed by Microsoft, offering real time fortification for your personal or business computer against malware, spyware, and viruses. Our anti malware finds and removes threats like viruses, ransomware, spyware, adware, and Trojans. 2 things are essential: another PC running the same operating system OS and a USB drive. While not the most potent antivirus product available, Microsoft Security Essentials serves as an excellent starting point for casual users. Your clients and staff rely on the security of the network to carry out day to day communications and business exchanges. We will notify you about your upcoming auto renewal via email. Click on “OK” to select it. For many businesses large and small, Windows Server may end up being the ideal server operating system. Smart Watches and Fitness Tracker ›. The changes will take effect immediately, so you won’t have to reboot or confirm another UAC prompt. Select the “Search” charm, and enter “Defender” in to the Search bar. We try to discern whether any of these extra features are particularly useful, or just frills that look nice but don’t serve a practical purpose. How to Disable Wi Fi Protected Setup WPS in Your Router. These include machine learning, behavioral analysis, application control and good file check. For every mention of “activeX controls”, set your selection to “prompt” or “enable. If there are apps that keep triggering UAC, use Windows Task Scheduler to run those apps without admin rights and UAC prompts first, instead of disabling UAC altogether. The changes will take effect immediately, so you won’t have to reboot or confirm another UAC prompt. You can find out more about which cookies we are using or switch them off in settings. As a default security option, you’re in safe hands. Your email address will not be published. Exe file to a different location random and retry the steps given above. We provide tech support to our clients. What Is UAC Virtualization.
Migena
The list is added with authorized PC friendly files after complete examination on a regular basis. This software runs as a service and can, therefore, be used for surveillance even when the program has been closed. Some users also reported that system file corruption should be blamed for the missing system registry file. Active Directory assigns a unique number to all security objects in Active Directory; including Users, Groups and others, called Security Identifiers SID numbers. Antispyware protection safeguards your usernames, passwords, and personal information. App Store is a service mark of Apple Inc. Actually, you might be surprised to learn that the free antivirus apps available from Avast, AVG, Avira and even Microsoft are just as good as those you pay for. Antivirus protects the system from viruses, whereas internet security covers a vast area of protection, covering spyware, viruses, phishing, computer worms, and more. Maybe worst of all, the sudden emergence of boxes everywhere because touchscreens had a huge push, despite this being no use on a typical desktop. Reliance on Microsoft to provide updates for things like Microsoft 365 after January 10 will officially be over. Access a list of archived CIS Benchmarks in Workbench.
Copyright © 2023 Small Business Software Reviews, Services Insight and Resources
For a free anti malware app, Microsoft Defender works pretty well. If you have Windows 11, see “How to protect your privacy in Windows 11. If the report matches a newly discovered malware threat with an unreleased virus definition, the new definition will be downloaded to remove the threat. Become the master of your Antivirus software by customizing your scan options based on your needs. In fact, these are all points we covered in our guide to securing Windows 7 past its support deadline. Developers often use available open source and third party software components to create a product; an SBOM allows the builder to make sure those components are up to date and to respond quickly to new vulnerabilities. The path you take is crucial. Fourth, make sure you have good backups of all your personal data. Administrators can manage all ESET endpoints, including mobiles, via one cloud based unified management console. He writes articles on SCCM, Intune, Configuration Manager, Microsoft Intune, Azure, Windows Server, Windows 11, WordPress and other topics, with the goal of providing people with useful information. Helps you customize your scanning schedule as per your convenient time. No taskbar icons or nothin’. If you are someone who often runs multiple applications on your PC. You can try it out and see if you can get the upgrade for free.
